Mounting Challenges to Geostrategic Access
3 Apr 2014
By Michael Haas for Center for Security Studies (CSS)
This chapter of Strategic Trends 2014 can also be accessed here.
The foundations of the US-sponsored global security system are crumbling. Prospective state and non-state challengers are steadily improving their ability to deny the United States, and its major allies, effective access to vital portions of the sea, air, space, and cyber domains. As their relative capability wanes and operational constraints accumulate, the deterrent value of forward-deployed combat forces is called into question. With its bedrock of military power exposed and subject to erosion, the future of the liberal security order is in the balance.
The durability of the US-centric system of global security provision is now a matter of growing concern for strategic planners around the world. At the source of their preoccupations are doubts regarding the ability of the system’s underwriters to sustain long-standing commitments in the face of increasing military and economic constraints. Chief among these are restrictions on the unmatched ability of the US armed forces – and, at a much lower level, those of first echelon allies like the United Kingdom and France – to position, sustain, and leverage superior combat power when and where it is needed. Some now fear that, as the global reach on which they ultimately depend is curtailed, established security arrangements will wither.
Several developments feed into this perception. As advanced military capabilities proliferate and emergent powers seek control over their environment, the United States’ military edge is blunted, as is also explored in the next chapter by Martin Zapfe. Simultaneously, shrinking defence budgets and contracting defenceindustrial bases accentuate the burdens associated with maintaining a meaningful level of qualitative superiority. Should regional actors succeed in carving out ‘contested zones’ that are beyond the effective reach of long-range power projection, the guardians of the geostrategic status quo will find it ever more difficult to shore up local allies and to counter revisionist initiatives.
In fact, China’s military modernization efforts are already beginning to neutralize core elements of the United States’ military access network, even as Beijing’s growing assertiveness along its periphery is stimulating the demand for US security provision. With forward bases exposed to missile attacks, carrier strike groups at risk from Chinese integrated defences, and battle networks susceptible to disruption, the operational advantages of the US military and its regional auxiliaries are melting away.
Much more circumscribed challenges are presented by a range of asymmetric warfare capabilities that smaller powers, such as Iran and North Korea, are fielding to reduce US freedom of action close to their shores. While they lack the depth and sustainability of a fully-fledged counter-intervention strategy, such approaches can nonetheless complicate the operational calculus of, and inflict substantial losses on, an intruding force. While it is likely to be accompanied by a level of self-deterrence and subject to important constraints, the availability to these actors of nuclear or chemical arms will not fail to further exacerbate these complications.
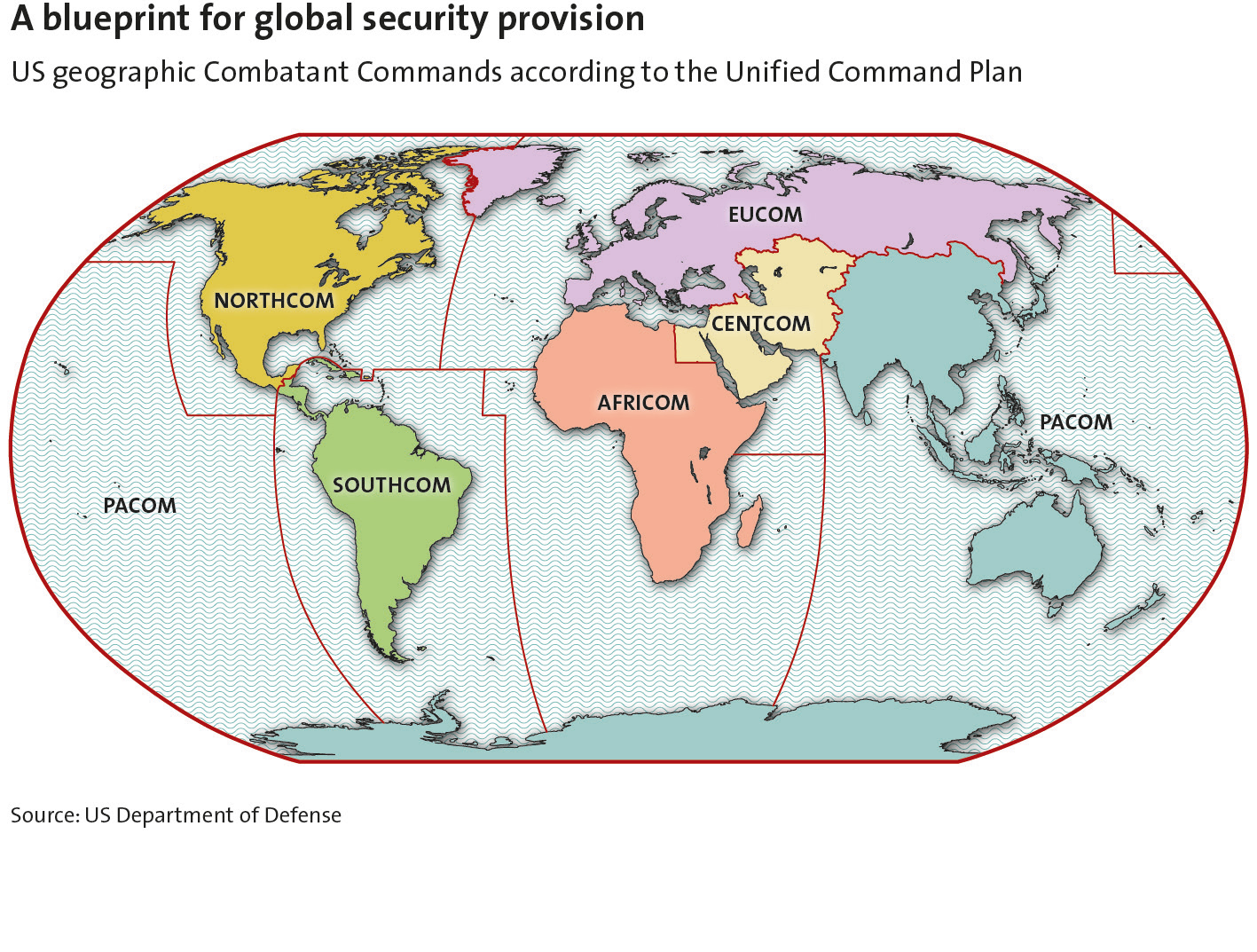
A Blueprint for Global Security Provision
Meanwhile, disruptive non-state actors continue to thrive in spaces of contested governance, some of which sit astride important lines of communication. Unlike capable state actors, their ability to deny major military powers access to their region is minimal. But as they acquire weapons of growing sophistication, the costs of military intervention into these spaces are rising and the chances of operational success are reduced. Likely imbalances in motivation and casualty acceptance serve to underline these restrictions.
From a European perspective, this heralds a period of growing uncertainty about future defence requirements and traditional modes of burden-sharing. With their relative military capability in precipitous decline, the global weight of European states is further reduced. But while the hegemonic bargains of old remain superficially intact, Europe is unlikely to wake up to the shifting requirements of global security provision any time soon.
The sinews of supremacy
Expeditionary military capabilities have played a fundamental role in shaping and sustaining successive incarnations of Western global supremacy. The United States, in particular, has built and maintained an extensive system of alliances and security partnerships supported by a large overseas military presence. This system has allowed the US and its allies to restructure the global security environment – centred on the core regions of Europe, the Middle East, and East Asia – to an extent that is quite literally without parallel in human history.
Outside their home regions, only America’s most capable allies – the United Kingdom and France – have been able to make a meaningful contribution to this effort, whereas such countries as Japan, Germany, Italy, Spain, Australia, and South Korea have acted as auxiliaries mainly at a regional level. It is only in the less stringent and more fragmented security environment of the post-Cold War era that the expeditionary impulse has become an important driver of force structure decisions for second and third echelon allies.
Like other hierarchical schemes for security provision before it, the current system is based on political commitments to defend its clients in the face of external threats, backed up by the credible combat potential of the security providers’ armed forces. While some have argued that the salience of military power in international politics is on the wane, it remains the sine qua non of collaborative security provision. However, where commitments are multiple and their geographic scope is extensive, force levels are rarely – if ever – sufficient to physically backstop all of them simultaneously. As in a banking system, potential liabilities always exceed the actual capabilities available to the creditor, often by a very significant margin. In dealing with this structural shortfall in the ultimate currency of security provision, the key requirements are strategic mobility and geostrategic access.
Strategic mobility is the linchpin of system maintenance, in both a physical and psychological sense. Only if security providers possess the factual ability to deploy, re-deploy, and leverage adequate military resources to shore up the system when and where it is necessary, can they hope to retain the trust and allegiance of their clients. In security systems that span several regions, such mobility has traditionally been provided by naval forces. Like the air forces by which they are now complemented, naval assets are either self-projecting or able to project other elements of a nation’s armed forces.
In order to project and sustain a substantial fraction of its combat forces overseas in support of its commitments, an outside power must secure geostrategic access – that is, the requisite freedom of action to establish and maintain a political-military presence within a given theatre. This presupposes the existence of sufficient projection forces, control over lines of communication to the theatre, and the availability of facilities for disembarkation, staging, and support, which can take the form either of temporary installations or fixed bases.
To effectively leverage his combat potential, the security provider must also assure access at the operational level, which results in the ability to conduct military operations with sufficient freedom of action and effectiveness to accomplish their aims. This requires that forces deployed into the theatre be survivable and logistically sustainable in the face of enemy action.
In hierarchical orders that consist of sovereign political units, access usually depends on the acquiescence of security consumers, who also tend to provide many of the facilities and services on which the security providers’ forward-deployed forces rely. To the extent that this is the case, security provision and geostrategic access are, in fact, mutually dependent.
While these arrangements are beneficial to all involved, the benefits are not equally distributed. Hence, the United States in particular gets vastly more out of its global military presence than does any single client or grouping of clients. In other words, the safeguarding of security providers’ national security interests and the provision of protective services go hand in hand. It is entirely plausible, in fact, that while they require effective military access to provide for the security of others, the system’s underwriters are in the security provision business mainly to gain and retain this access for their own non-altruistic purposes.
To guarantee the integrity of these arrangements, the US and its major allies have consistently acted – from the Korean War to the Persian Gulf War to the ongoing island disputes in the East and South China Seas – to avert emerging military challenges and prevent other powers from carving out exclusive rights that could diminish their strategic prominence. However, as Western economic, military, and ideological dominance gives way to a more polycentric distribution of power, the days of unfettered access are almost certainly coming to a close.
Denial dawning
US security provision efforts, whether undertaken unilaterally or in concert with the more capable among its allies, have never gone entirely unopposed. In past decades, rudimentary cost-imposing strategies have attained modest successes in several instances.
During Operation Desert Storm, Iraq utilized low-cost and obsolete moored mines to limit coalition naval forces’ operational freedom of action inside the Persian Gulf. While the overall impact on naval operations was limited, a guided missile cruiser and an amphibious assault ship were severely damaged by mine strikes. The employment of Scud-type ballistic missiles against allied staging areas and political centres of gravity entailed both direct and indirect costs, including the diversion of significant US resources.
During the Kosovo War of 1999, Serb air defence forces proved extremely adept at limiting their exposure to NATO’s suppression of enemy air defences (SEAD) and limited the alliance’s operational freedom of action throughout the campaign. As a result of force protection measures taken in response to the persistent surface-toair threat and Serb deception, NATO air forces failed miserably in their efforts to destroy mobile military targets inside Kosovo itself.
Also, in October 2000, an Al-Qaida terrorist cell struck the guided-missile destroyer USS Cole, while it was refuelling inside the Yemeni port of Aden. Utilizing a primitive shaped charge placed inside a small boat, the suicide attack inflicted severe damage and killed 17 US sailors, with another 39 injured in the blast.
As none of these attacks were indicative of serious constraints on either geostrategic or operational access, they are better conceptualized as limited attempts at area denial. In fact, in the unipolar international order that took shape in the immediate postCold War era, US and allied freedom of action was never in serious dispute. Yet, as the full weight of Western power projection – unconstrained by any meaningful geostrategic counterweight and enabled by the burgeoning informational revolution in military affairs – became apparent, countervailing tendencies of a far more sophisticated nature began to stir.
With the Iraqi and Serbian defeats fresh in their minds, potential targets of Western military interference – prominently including the Chinese People’s Liberation Army (PLA) – began to invest in capabilities and operational frameworks designed with the sole intent of offsetting US and allied superiority at acceptable cost. As they expand the means and diversify the approaches available to them for access denial purposes, these efforts are now beginning to bear fruit.
Entrepreneurs of exclusion
As it is through the forward presence of its military establishment that the dominant role of the United States in the security affairs of the three core regions is maintained, the only reliable way for a challenger to reduce this role is to be able to negate its military component. Several key vulnerabilities present themselves for exploitation. Above all else, the current access regime is highly dependent on a relatively small number of forward bases and carrier battle groups. In quantitative terms, most of its forward-deployed striking power is concentrated in short-range aircraft. Finally, the entire system is held together by vulnerable space assets and computer networks that are almost certainly susceptible to some degree of disruption.
Most of the military anti-access approaches that are currently in evidence directly target one or several of these vulnerabilities. In doing so, they are harnessing two major sources of military change: proliferation dynamics in the area of advanced conventional weapons and doctrinal innovation. While the former provide a growing number of actors with increased levels of capability to inflict damage on a capable opponent, it is the latter that ties these military-technological potentials into a system that provides operationally significant combat power.
As far as the ‘hardware’ component is concerned, most analyses emphasize a number of key capabilities that are seen as constituting the core of a ‘modern’ anti-access defence: Sophisticated anti-ship missiles (ASMs) and extended air defence systems provide a means of keeping all but the stealthiest and most survivable attack platforms at bay. Equipped with advanced torpedoes and mines, as well as longer-range ASMs, the presence of even a few silent diesel-electric submarines can disrupt an intruder’s sea lines of communication and seriously complicate forward operations. Conventionally armed ballistic missiles are an ideal asset for attacks against well-defended area targets, such as airbases. Meanwhile, antisatellite (ASAT) weapons and other means of information warfare could severely degrade the command and control (C2), intelligence, surveillance and reconaissance (ISR) as well as precision targeting without which the tightly coordinated and fast-paced operations preferred by Western militaries are bound to falter.
The technological basis for such defensive advantage is, however, highly variable. Even obsolete weaponry of little independent value can be used to great effect, if it is properly integrated into a suitable doctrinal framework for its use. So embedded, the range of instruments that can be utilized for anti-access or more limited area denial purposes is very broad indeed – potentially including anything from an explosive-laden dinghy to a full-scale thermonuclear weapon. Therefore, successful approaches are not likely to be dominated by any single element, no matter how novel or impressive.
More than their individual components, it is the complexity of the challenge that the intervening power is presented with – the tactical and operational dilemmas which it entails – that makes such approaches difficult to overcome. In this regard, idiosyncratic mixtures of high-tech and low-tech instruments may prove particularly successful in disrupting the preferred patterns of Western military operations.
Engineering a high-end challenge
Over the last two decades, the military organization that has made the most progress in creating a multi-layered system for access denial is China’s People’s Liberation Army. Under the long-standing monikers of ‘active defence’ and ‘local wars under informatized conditions’, the PLA is now fielding a diverse portfolio of missile, air, and naval forces optimized for counter-intervention operations in the narrow seas along China’s periphery, and in the Taiwan Strait in particular. In fact, this effort has become an archetype to which analytical treatments of current access denial challenges overwhelmingly have reference.
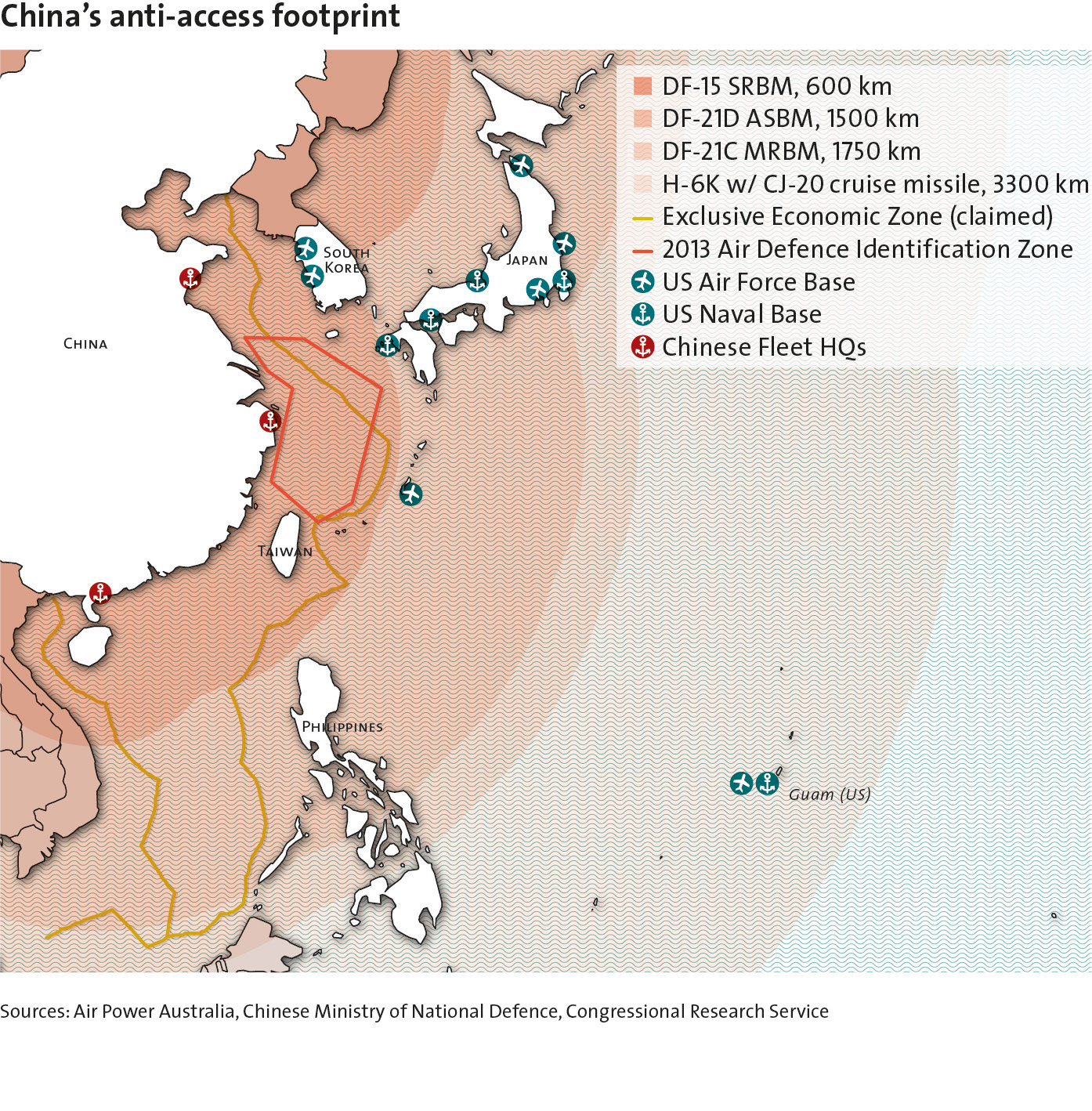
While it includes most of the ‘core’ capabilities commonly associated with anti-access and area denial, some elements of the Chinese approach have been singled out as being particularly significant. Chief among these is the world’s first partiallyoperational anti-ship ballistic missile (ASBM), a variant of the mediumrange DongFeng(DF)-21 that is currently being introduced into the PLA’s Second Artillery Force. Carrying a manoeuvrable re-entry body, it is designed to disable a large, moving surface target – such as an aircraft carrier or one of its escorts – over ranges in excess of 1500 kilometres. With landbased firepower reaching this far into the high seas, naval operations may no longer be dominated by surface warships in a 21st century setting.
Given that the effective range of current and projected carrier aircraft is significantly shorter, and airbases in the region would probably be under simultaneous ballistic and cruise missile attack, this presents a major challenge for the United States’ regional posture. In conjunction with other landand sea-based systems, the ASBM could throw a protective umbrella over Chinese forces operating in the South and East China Seas. US attempts at re-establishing control over denied areas would initially have to rely on a very limited range of assets, including its attack and cruise missile submarines, and its small fleet of stealthy B-2 bombers. Moreover, as a land-based system enabled by sensors deployed in space, direct attack on any element of China’s ASBM capability would raise daunting issues of escalation control.
China's Anti-access Footprint
Another focal area of China’s access denial efforts has been its anti-satellite programme, which should be seen as part of a broader preoccupation with offensive information warfare. Besides its kinetic ASAT capability, the PRC is also thought to have developed non-kinetic means of disrupting the space-based enablers on which the US military critically depends. As a kinetic offensive in space would invite US retaliation in kind, and produce enough destructive debris to permanently impair both civilian and military uses of space, a focus on the latter variants would seem to provide the rising anti-access power with more attractive lines of effort.
China is also known to have one of the world’s most active programmes for cyberwarfare and espionage, and has already scored major successes on this front. According to an official US government report, this includes the theft in recent years of highly classified data relating inter alia to the Joint Strike Fighter, the Littoral Combat Ship, the Terminal High Altitude Area Defense anti-missile system, and more than 20 other major defence acquisition efforts.
However, in the current debate, cyber operations are being emphasized at the expense of a broader concern with the electromagnetic spectrum at large – that is, electronic warfare (EW) in all its various dimensions. As far as actual combat is concerned, the impact of EW on vital command, communications, and targeting functions is likely to significantly outrank that of cyberactivities, narrowly conceived. Conversely, the benefits of effective countermeasures will be more tangible in this well-established but widely underappreciated area of military operations.
Overall, it is critical that analysts develop an integrated understanding of these various capabilities, and of the basic strategic tendencies and operational inclinations that they reflect. Perhaps most worryingly, there is evidence of a strong preemptive streak in the Chinese conceptualization of anti-access warfare, which depends on the shaping effects of early offensive operations to overwhelm a US and allied posture that is still markedly superior in most respects. It would thus seem that the PLA is setting itself up for a destabilizing competition to ‘get in the first blow’ – a competition that an offensively-oriented US Navy and Air Force are unlikely to spurn.
Pushing back with limited means
If China has become the paragon of full-scale access denial, the best examples of lower-level approaches to counter-intervention are currently presented by Iran and the Democratic People’s Republic of Korea (DPRK). While both of these countries are severely hampered by economic infirmities and technological barriers, they are now deploying an array of low-cost forces designed to complicate an intervening power’s access requirements as it closes in on their respective territories. While these measures are likely to crumble under the concentrated blows of US power projection, supported in both regions by increasingly capable regional allies, they may well shift the balance of mutual deterrence in favour of the local challenger.
The Iranian and North Korean antiaccess approaches have several major elements in common. Firstly, both countries are fielding large arsenals of conventionally armed ballistic missiles that serve as partial compensation for their deficits in combat aviation. Based on essentially the same Soviet-derived technologies which were passed on to Iran by the North Koreans, these arsenals each consist of hundreds of Scud-type short-range missiles and a significantly smaller number of medium-range missiles.
All of these weapons are likely to be effective only against large area targets and, because they are hardly immune to interception and their radius of damage is small relative to any conceivable target, only when fired en masse. However, when targeted at large military installations or civilian infrastructure, they can cause substantial disruption and impose costs that the intervening power may well consider unacceptable. In conjunction with other instruments, they can thus be expected to serve as a valuable deterrent in many lower-level crisis situations.
A second key element in both the Iranian and North Korean approaches is asymmetric naval capabilities. While Iran’s conventional navy is weak, with surface forces made up of obsolete platforms that would fall an easy prey to any capable adversary, it controls the only submarine fleet in the region. Composed of a small number of modern, Russian-built diesels as well as domestically-built coastal and midget submarines, this is a force to be reckoned with in the confined and shallow waters of the Gulf. Given the extremely difficult sonar conditions that are likely to prevail there, US and allied anti-submarine efforts are unlikely to yield quick results.
Perhaps even more difficult to counter are the unconventional naval forces of the Pasdaran (or Iranian Revolutionary Guards Corps), which comprise as many as 150 fast patrol craft, most of which are well-armed. Like the submarine force, their operations are aided by the favourable geography of the Gulf. With a doctrine of highspeed, decentralized operations, these swarms of small boats could make for a cramped and volatile tactical environment.
North Korea’s naval force structure is somewhat similarly balanced, comprising even larger numbers of both surface and sub-surface units. While these vessels have scant chances of survival against a first-class navy, the 2010 sinking of the South Korean corvette Cheonan by a DPRK midget submarine underlined the cost-imposing potential possessed even by lowvalue asymmetric assets.
By distributing their firepower in so many small packages, each one of which is individually expendable, Iranian and North Korean naval forces are leveraging the proximity advantage of the local defender and countering the superiority of the major surface combatant with speed, concealment, surprise, and sheer numbers. Crucially, as the intruder closes in on the defender’s shores, the coastal state can also bring its land-based firepower to bear in support of such distributed naval operations.
A third element that both states emphasize is passive defence, which provides an extremely cost-effective means of limiting their exposure to Western strike warfare from the air and sea. Iran is known to be a leading maker of ultra-high-performance concrete for both civilian and military applications, and has moved major elements of its nuclear and missile programmes underground for fear of Western air attack. North Korea has deployed much of its front-line heavy artillery in caves and other hardened firing positions to protect it from allied counter-battery fire, and is almost certainly storing any nuclear weapons components inside extremely hard, or deeply buried, facilities.
While the US armed forces in particular have made defeating such methods a priority mission, and are fielding both conventional and nuclear weapons developed for this specific purpose, the advantage here lies with the defender. In fact, when covered by thick-enough layers of solid rock, such facilities may be beyond the reach of even a megaton-class thermo-nuclear warhead.
While they are not without limitations even at the tactical level, nuclear weapons constitute an extremely potent counter-intervention capability. Both Iran and North Korea have invested a significant portion of their limited resources in this area, and have been targeted by US and allied coercive diplomacy to avert their acquisition of these ‘ultimate’ weapons. So far, only the DPRK has succeeded in creating an embryonic nuclear arsenal and delivery system. Meanwhile, Iran’s attempted development of a precursor capability has been slowed down by stringent non-proliferation efforts and is currently subject to extensive international controls.
As is evident from these two cases, as well as several other failed acquisition attempts, international pressure – not entirely coincidentally orchestrated by the United States and its major allies – now presents would-be nuclear powers with significant and possibly insurmountable obstacles. The possession and use of chemical weapons, which could also constitute a potent disincentive to intervening powers, is also being targeted by global norm-enforcement efforts. Moreover, overreliance on such highly escalatory instruments would confront inferior powers with unpleasant choices should deterrence ever fail.
It is therefore likely that conventional weaponry married to asymmetric operational concepts will continue to dominate the ‘anti-Western way in warfare’. In Iran’s case, the salience of these approaches in its defence strategy will undoubtedly increase further as additional restrictions are imposed on its nuclear work. Its attempts at acquiring a credible ASBM capability of its own – though unlikely to succeed in the near term – would seem to point in this direction. In those cases where they are present, nuclear and chemical weapons will no doubt impose considerable limitations on access operations and present delicate challenges for escalation control.
Missiles from the void
A final challenge to Western geostrategic access is presented by non-state and hybrid actors and their ongoing quest to assert control over spaces of contested governance. While the long war on global Islamic jihadism has led to an unprecedented expansion of US and allied ‘shadow warfare’ activities, both territorially organized and transnational militant groups of this type continue to thrive throughout the greater Middle East, in East Africa, and beyond.
In some respects, deep US and allied interference in these regions is now proving profoundly counterproductive. Having plundered the arsenals of the decaying autocracies in Libya and Syria with the infelicitous assistance of Western governments caught up in normative pretensions of their own making, and receiving state support from Western allies in the Gulf region, a number of militant groups are now increasing their operational reach and expanding their arms portfolios.
The most impressive example of the recent growth in non-state military capability, however, remains the Hezbollah militia. With generous backing from Syria and Iran, the ‘Party of God’ has not only amassed tens of thousands of artillery rockets, which now make it the first non-state actor to possess a fully-fledged strategic attack capacity vis-à-vis a sovereign state. It has also proved itself capable of contesting Israeli operational access from the sea by launching several Iranian-supplied ASMs at the missile corvette INS Hanit during the 2006 Lebanon War. Reportedly, this limited potential for anti-shipping operations has recently been augmented by samples of a much more formidable weapon system, namely, the advanced Yakhont ASM sold to the Assad government by Russia in late 2011.
In another notable incident, in September 2013, an Egyptian militant group of much lesser stature succeeded in attacking a container vessel transiting the Suez Canal. While the attackers’ use of rocket-propelled grenades serves to underline the comparative feebleness of their organization and is hardly indicative of an acute threat to Canal shipping, this incident may well be a portent of more ominous developments to come.
In combination, these recent developments herald a future in which nonstate actors can not only complicate or defeat military ground operations on their home turf, but also besiege strategic chokepoints and dispute command of the sea out to several hundred kilometres from the shores they control.
The great contraction
Meanwhile, in the light of constricted budgetary environments and spiralling modernization costs, the proponents of the geostrategic status quo are finding it ever more difficult to maintain a significant technological edge over prospective challengers. While military forces occupy centre stage in the struggle for geostrategic access, it is economic factors that now represent the greatest impediment facing Western security providers’ adaptation efforts.
The root causes of this particular challenge are global shifts in latent power resources and fiscal irresponsibility at home. This includes a long-standing, and increasingly fatuous, tendency to let defence acquisition costs spiral out of control. This means that the defence budgets of the US and its allies are shrinking in both absolute and relative terms, while also buying less on a dollar-for-dollar basis.
As a result of these developments, military adaptation in the face of more stringent access requirements and growing vulnerabilities is taking place within the confines of a fiscal straightjacket. In the United States, the impact of the Budget Control Act of 2011 – which comes on top of earlier substantial cuts made by Secretaries Robert Gates and Leon Panetta – is already being felt throughout the force. The UK is undergoing the most radical defence consolidation in its recent history, which has led to the temporary elimination of its carrier force and a further constriction of deployable combat power. In France, defence spending will be held constant for the next several years – something of a best-case outcome given its current economic travails.
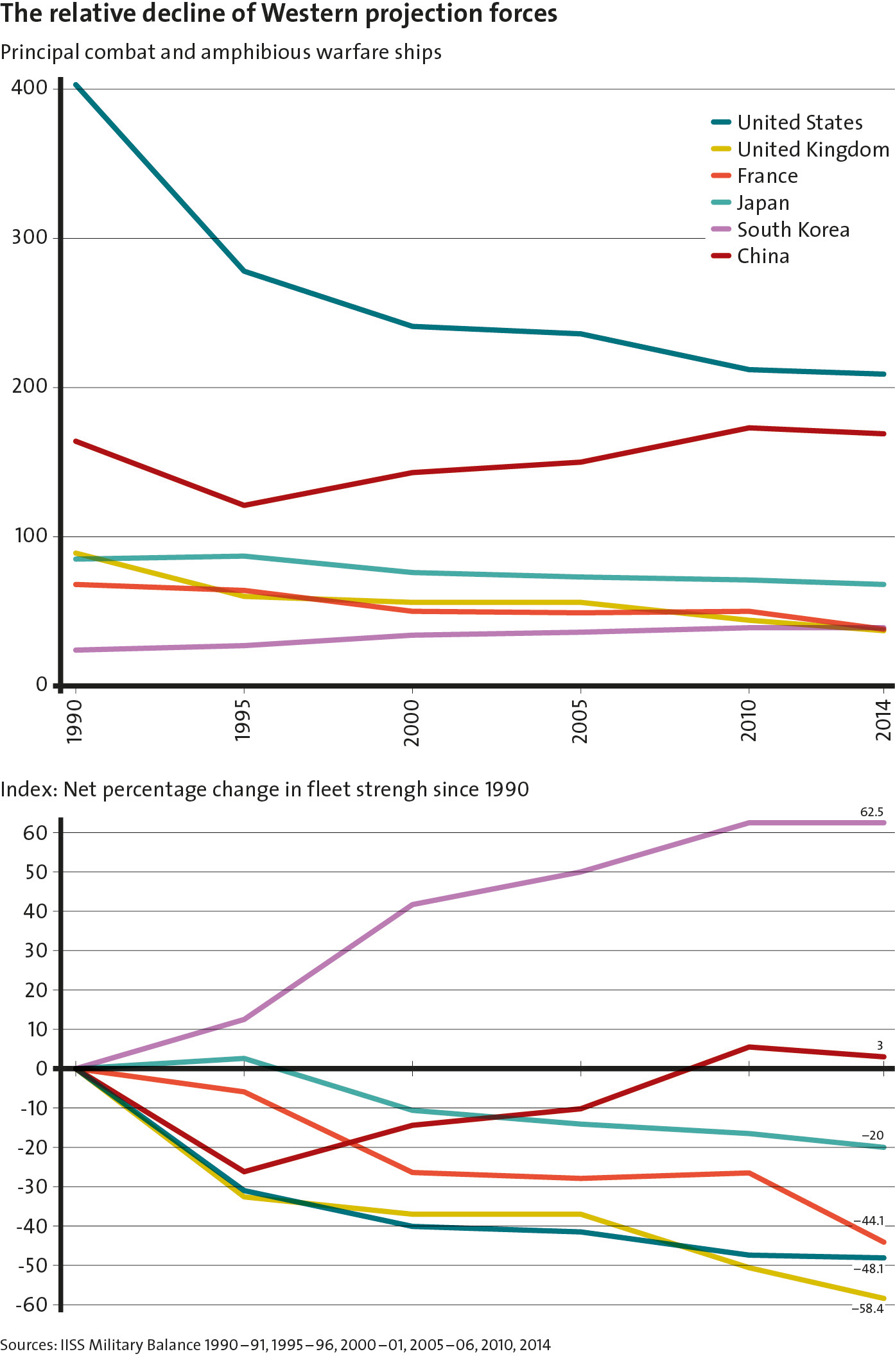
The Relative Decline of Western Projection Forces
With budgets stagnant or in decline, and acquisition costs on the rise, the security providers are working themselves into a structural dilemma: They are building ever smaller numbers of ever more expensive platforms with which to accomplish the same, or even more demanding, missions. While these platforms are undoubtedly becoming more capable, numbers matter profoundly. Even with greater availability and combat power, the Royal Navy’s six Type 45 destroyers will not be able to provide the same level of forward presence as the twelve Type 42 destroyers they are replacing. With shrinking force levels, the significant military powers of the West become less able to provide assurance and react to emerging threats in a timely manner.
In addition, the growing debate regarding the survivability of nonstealthy platforms that is fuelled by the rise of anti-access warfare suggests that the self-deterrence entailed by this tactical vulnerability may well be transformed into a crippling ‘strategic’ vulnerability. As security providers become less willing to risk their expensive assets, in which an ever increasing share of their capability is concentrated, their forward posture becomes less credible and the psychological foundations of security provision are weakened.
Even where doctrinal and acquisition priorities are adjusted to the emerging requirements, as is clearly the case in the US armed forces, fiscal constraints and serious faults in the acquisition process take their toll. To provide just one example, the US Navy’s nextgeneration DDG-1000 destroyer programme was pared down from an initial requirement for 32 hulls to a mere three, with steep increases in costs per unit actually built. Orders for the Littoral Combat Ship, of which 52 were planned, have been cut to 32. The F-35 programme – the most expensive in American history – is also moving ahead despite doubts about the operational value of a relatively short-range aircraft in access-constrained environments. Irrespective of these concerns, it will consume the single largest share of the funds set aside for countering anti-access approaches as part of the joint AirSea Battle concept for many years to come. Meanwhile, the acquisition of a new long-range bomber to replace the B-2, of which just 19 are in service, is proceeding at a glacial pace.
As a renovation of the governmentalmilitary-industrial partnerships remains elusive, the best option from a US perspective may be to shift the economic and military burden of security provision to its regional auxiliaries that are directly impacted by prospective challengers’ anti-access measures. However, it would appear that, in the medium term, US leadership of the global security order will be difficult to sustain except on a basis of fiscal prudence.
An age of vulnerability?
In the face of a diverse set of challenges to geostrategic access, some now fear that the geopolitics of openness that has shaped the global system of the post-World War II era is gradually being replaced by a new geopolitics of exclusion. Challenges vary from domain to domain, but the aggregate picture is of an operational environment that will be more complex, and markedly less permissive, than that encountered in most conflict settings of the postCold War era.
While potential challengers of Western military dominance are fielding a number of impressive capabilities, any attempt at defining access denial in terms of a particular set of hardware or tactics is likely to be of limited value. In fact, what most clearly sets these approaches apart from other paradigms of military operations is their basic rationale of counter-intervention. Whatever means are likely to serve that particular end should be seen as possible ingredients of actors’ attempts at tilting the balance of military advantage in favour of a regional area defence. Therefore, countermeasures based on increased flexibility and adaptability are likely to yield greater benefits than narrowly technical solutions to specific problems.
In strictly military terms, even China’s full-scale approach to counter-intervention must be seen as an expression of continued inferiority vis-à-vis the United States and its regional security partners. However, current challenges appear focused on reshaping regional security arrangements in peacetime, rather than on the institution of exclusion zones in wartime. Thus, it is primarily on regional actors’ perceptions of the military balance that the integrity of the US-centric security order now hinges.
With ongoing changes in both its military and economic parameters, the system’s resilience in the face of growing pressures is not assured. At the very least, the confluence of external and internal restrictions will render the maintenance of geostrategic access an even more prominent concern. A partial redistribution of responsibilities among the US and its regional partners will probably be inevitable if the basic shape of the incumbent system is to be maintained.
On the other hand, irrespective of how China and other rising powers develop, a militarily viable hegemonic alternative to US security provision is not currently in the cards. In addition, it should be noted that Western control over vital areas of the sea, air, space, and cyber domains has always been, and will remain, a matter of degree.
From a European perspective, the erosion of the United States’ military preeminence would seem to present the ‘old continent’ with the structural opportunity to re-assert itself as an independent force in global security affairs. However, with its indigenous projection capabilities in precipitous decline and its weakness compounded by complacency, Europe’s ingrained reliance on hegemonic subventionism is likely to persist, even as we enter this new era of systemic vulnerability.